Can flagging new domain names help stop the spread of malware?
In fact, many malware networks are programmed to frequently register new domain names to keep one step ahead of blacklists*.
Boeing (NYSE:BA), a company that is certainly a target for malware attacks, has come up with a creative solution to weed out these potentially harmful links without relying on out-of-date URL blacklists.
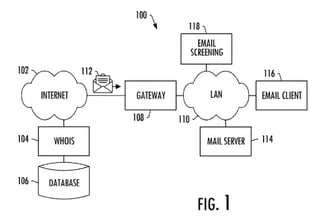
In a patent application (pdf) filed last year and publised by the U.S. Patent and Trademark office today, the company outlines a way to flag links in emails from what it calls “newborn” domains.
Basically, a service will ping whois to check the registration date of any domain names linked to within an email. If they are within a set timeframe, the email server could remediate risk by disabling the link, providing a warning to the recipient, or not delivering the email.
It’s an amazingly simple idea that I hope is put into commercial use.
* On the same day Boeing filed its patent application, Cisco filed one (pdf) for detecting domain names registered as part of these systems.






It looks like they were pretty quick on the draw within a few weeks after Paul Vixie presented this:
https://www.rsaconference.com/writable/presentations/file_upload/hta-r02-domain-name-abuse-how-cheap-new-domain-names-fuel-the-ecrime-economy_final.pdf
Huh. Perhaps that’s where Cisco got its idea as well
Another example of patenting the bleedin’ obvious.
My mail server just downright blackholes anything from .xyz and a few of the other domains that are sold at a discount and are used for not much else other than spamming. .top .download .date .bid .men and .stream spring to mind.
How long until hackers start phishing with using domains bought for $5 at GoDaddy Closeouts or other discount domain marketplaces? Would bypass the age problem nicely for them, no?
Every domain at GD Closeout is at least a year old and many much older with a history of legitimate email usage.